Reading time: less than 1 minute

It is widely known that the Internet is flooded by constant cyber attacks. Once connected to the Internet, the devices will face all kinds of security problems. Therefore, it is generally recommended that the devices are not connected directly to the Internet, unless there are special-purpose access. No direct access to external network, the likelihood of being attacked device will be greatly reduced. Yet, this does not preclude the possibility of an attack. When it is necessary to make a device to be visible over the internet, it is important to protect it using a deep approach to defense. Firewalls, VPNs, Intrusion Detection, encryption and two-factor authentication for Internet access to devices, are effective ways to reduce the risk of attack and alerting the abnormal network traffic.
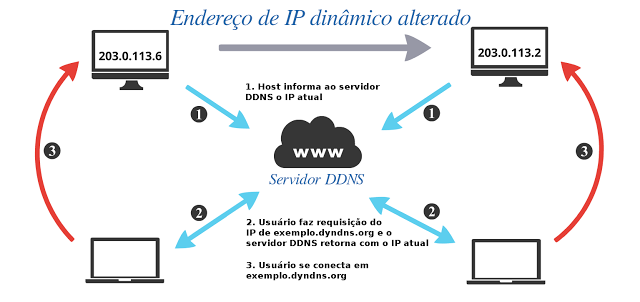
If the P2P or VPN solutions do not meet users' needs, who wish to have a quick and continuous access to port service specified the device via the Internet, users may have to choose the traditional scheme “Port Forwarding”. While this provides easy access to devices, It should be given special attention to security controls, because these devices will be visible from the Internet. If someone decides to use this method, it is highly recommended that other security controls on the host to be used to better protect the device. As shown in guides “IPC Security”e” NVR Security”, the Hikivision provided a number of recommendations to better protect these devices:
1) Minimize the number of ports exposed to the Internet. Do not configure the IP address of the DMZ device, which will expose your device directly to external network. Only forward the network ports that should be used. For example, to use Web services, only port 443 it is forwarded.
2) Avoid using generic ports and reconfigure them as custom ports. After you changed the default port, you will reduce the risk that the attacker
guess the port you are using. For example, the door 443 It is generally used for HTTP. It is recommended that you configure a custom port for the service instead of port 443, and the custom port must be in accordance with the TCP port rule / IP (1 – 65535).
3) Enable IP filtering. If you have static IP addresses on their mobile devices, you can create a filter rule with an IP range (Your Internet service provider at home, your mobile phone
service provider, etc.) and allow only devices in the specified IP address filtering rule to access the system.
The above safety tips can increase security to some extent, but these are not enough, and users still need to do the following as basic points:
1) Set a strong password. See the NIST's recommendations for strong password creation. https://pages.nist.gov/800-63-3/sp800-63b.html
2) Upgrade to the latest firmware of the device released by Hikvision, as soon as possible.
If possible, put your Internet-connected devices behind a VPN can improve system security substantially. While Hikvision devices currently do not have integrated VPNs, you can deploy VPN servers in front of the devices.