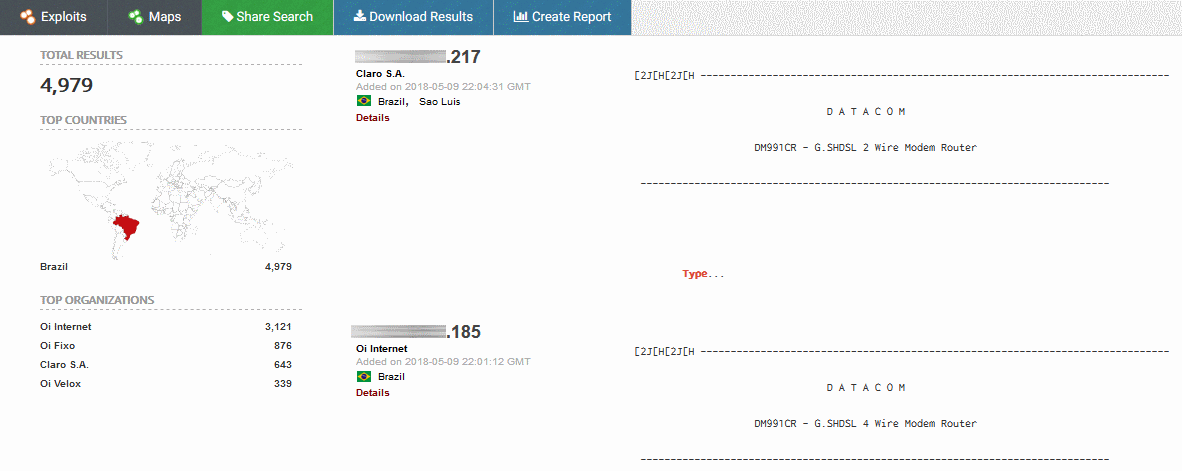
A Brazilian ISP seems to have deployed routers without a Telnet password to almost 5.000 customers, leaving open devices to abuse.
The devices were discovered by Ankit Anubhav, Principal Investigator of NewSky Security, a cyber security company specializing in security Internet of Things.
All exposed devices are routers that Datacom ISP – Oi Internet – provided to customers. Anubhav says it has identified three types of routers Datacom – DM991CR, DM706CR and DM991CS.
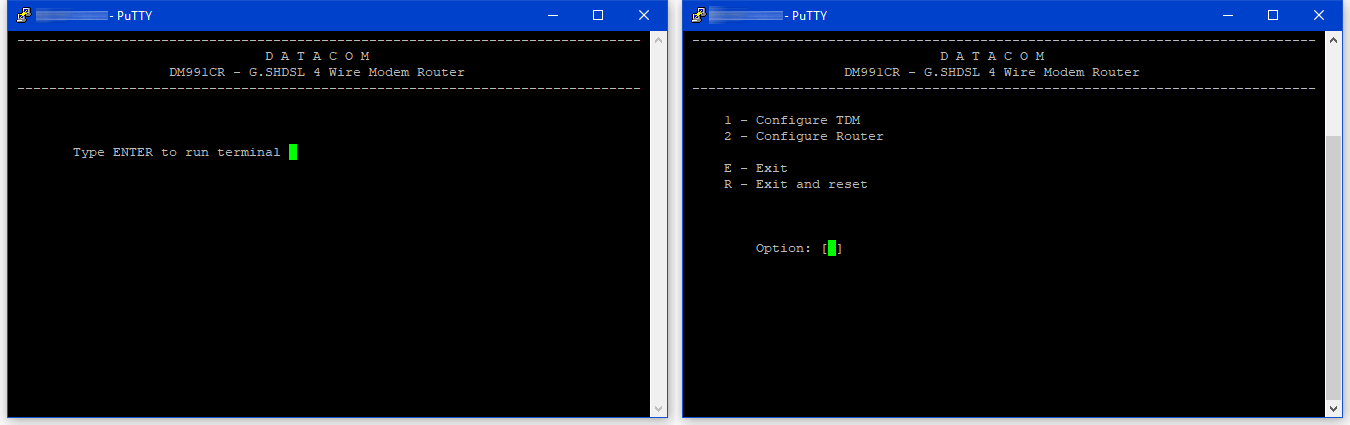
Enter ENTER to hack
Some devices had a Telnet password, but most allow anyone to alter signed in to the router and its configuration.
“This is not a problem with the device architecture, but a bad configuration of devices, since its telnet is exposed to the outside world without any challenge”, Anubhav disse to Bleeping Computer.
The researcher pointed to one of the router manual that suggests that the devices come with a Telnet service with no password by default, which means that users must set up one myself.
The Bleeping Computer tried to contact the Hi Internet, but they were greeted only by robots automated chat and staff who did not speak English. The NewSky Security told Bleeping Computer that notified the CERT Brazil on routers exposed, requesting that the local agency contact him the operator with their findings and present a solution to protect the exposed devices.
Take control of the devices is a piece of cake
Take these routers is very easy for attackers, they can write automated scripts that take advantage of the lack of a Telnet password to net routers exposed in a botnet.
“The IoT attacks can be simplified into three levels: Level 0 (device without authentication header), Level 1 (guessing a weak password / pattern) and Level 2 (using an IoT operation to gain access)”, explica Anubhav.
“Although IoT attackers are becoming more sophisticated with time, with NewSky Security seeing an increase in the level of attacks 2, We can also observe that the easiest attack vector (using a level of attack 0 for controlling a device authentication) It is still very relevant in 2018 , thanks to the owners exhibiting their devices without even set a password. ”
“Set a strong password and keep your updated IoT device limits the invaders to use a day brutality session zero or long, both options are not very profitable for most invaders, making the device safe”, He added the expert.
The Bleeping Computer refrained from sharing the Shodan search queries that expose these devices to give owners of devices and ISP longer to protect their devices.
Source: www.bleepingcomputer.com